With recent spate of vulnerability disclosures in the Adobe Reader and Acrobat programs it is time to take a big picture look at the PDF (Portable Document Format) format. The first observation that I make is that the PDF is not a strictly a static file; because of its potential for embedded JavaScript actions, it is an executable program. Since it is an executable program it needs to be treated as such from a security perspective. We need to have virus scanners aware of the executable functions within PDF files and warn us or inoculate us against the executable code that exists in the format.Most people assume that a PDF file is a safe, immutable way to save and transmit unstructured information. Unfortunately because of the ability to create forms and JavaScript actions the PDF file has moved far beyond that; which is why the format has become so vulnerable to hackers. One solution that would stop this problem in its tracks would be for Adobe to create two different formats (PDF and PDX for example) and remove the JavaScript capabilities from the core PDF format. Until that happens we need to be wary of PDF files and take some of the following steps:
- Educate the user community that PDF files are inherently unsafe and should be treated with caution
- By default, disable the functionality to run JavaScript within Adobe Reader and use it only as an exception.
- Make sure that we have prevention tools in place to detect rogue PDF files.
- Make sure that we have deployed detective controls to notice when unusual behavior is taking place on a user’s workstation or on the network so that we can fight off the PDF-borne attacks.
For those who are interested in the latest patches, Adobe issued updates yesterday for Adobe Reader and Acrobat that deal with the Critical security issues that have been discovered in the current release 9.3.2 (and earlier versions). Here is the security bulletin from Adobe with links to version 9.3.3 of the software products.
In running Varonis DatAdvantage there are times when you want to look at the history of the nightly jobs for a longer period then the defaults provided by SQL Server 2005. These defaults are based on 'Maximum job history log size (rows)' and 'Maximum job history rows per job.' If you are monitoring a large number of servers than the system may only keep several days worth of history for each job. Where disk space on the SQL Server is not an issue one change the the delete option to purge data based on an overall duration, which can be specified in days, weeks or months. For example, we might want to retain 10 days worht of history to assist in debugging issues. To do that perform the following steps.First run SQL Server Management Studio.
Then navigate to:
• Root
• SQL Server Instance
• SQL Server Agent
• Right click on SQL Server Agent 
- From here right-click on history.
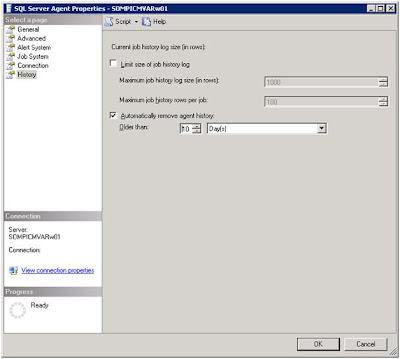
- Select the option to "Automatically remove agent history" and enter the duration that you want to keep the job history.
- Click on OK and you are ready to run.