Like most of us, I receive invitations from random folks on the Internet asking me to connect with them via LinkedIn. In some cases they are from accounts with no connections and no reasonable profile. They are clearly looking for information for nefarious purposes. Yet when the email comes in, this is all that LinkedIn says:
"WHY MIGHT CONNECTING WITH SHAMSODIN KARIMI LASAKI BE A GOOD IDEA?
shamsodin karimi lasaki's connections could be useful to you
After accepting shamsodin karimi lasaki's invitation, check shamsodin karimi lasaki's connections to see who else you may know and who you might want an introduction to. Building these connections can create opportunities in the future."
What is LinkedIn thinking? Why encourage me to connect with a potential hacker?
Social networks lose their effectiveness when people lose trust in the overall experience and it is LinkedIn's best interest overall the long run to discourage people from connecting with people they do not have a relationship with.
Let's encourage LinkedIn to add a warning to those emails as well. Here is one potential idea.
"WHY MIGHT CONNECTING WITH SHAMSODIN KARIMI LASAKI BE A BAD IDEA?
If you have no freaking idea who LASAKI is, he might be trying to gather personal information from you as part of a plan to launch a spear-phishing attack against you or one of your connections. Building these connections with people you do not know can create risks and privacy concerns in the future."
Tips on Improving IT Security and System Administration from Castle Ventures Corporation.
Sunday, December 18, 2011
Saturday, November 19, 2011
Tracking AD Groups Changes with Varonis
Varonis DatAdvantage tracks changes in Active Directory group membership by comparing the results of the nightly AD walks. If we want to see the changes that have been made to a user we can use the "1a - User Access Log report." The key filter to remember is that we want to show data from the "History of Differences." This shows the changes that have been picked up by the nightly jobs. Then we need to select the date range that we want to look at.
Then select the "Operation Type" filter. There are two operation types that we can select depending on what we are trying to track:
The final piece is that the user affected by the change is identified in the "Change Description" field. Use the "Like" operator and remember to enter in the domain name before the start of the user name.
Run the report and you have the answer you were looking for.
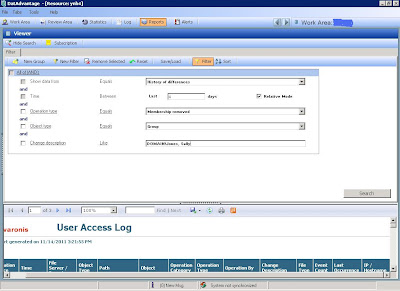
Note: Starting in Version 5.6 of Varonis DatAdvantage we also have the "3e - Historical Group Membership" which will display the groups a user belonged to on a specific date. Great report for answering those tricky audit questions.
Then select the "Operation Type" filter. There are two operation types that we can select depending on what we are trying to track:
- Membership Removed
- Membership Added
The final piece is that the user affected by the change is identified in the "Change Description" field. Use the "Like" operator and remember to enter in the domain name before the start of the user name.
Run the report and you have the answer you were looking for.

Note: Starting in Version 5.6 of Varonis DatAdvantage we also have the "3e - Historical Group Membership" which will display the groups a user belonged to on a specific date. Great report for answering those tricky audit questions.
Friday, July 8, 2011
UCLA Health System Settles Potential HIPAA Privacy and Security Violations
The Department of Health and Humans Services reached it third settlement this year with a healthcare organization for violations of the HIPAA regulations when UCLA agreed to pay $865,000 to resolve charges that employees were inappropriately snooping into the records of celebrity patients.
In the previous settlements of 2011, Massachusetts General agreed to pay a fine of $1,000,o00 and Cignet Health of Prince George's County agreed to a fine of $4,300,000. Clearly HHS is taking these violations much more seriously than had been done in the first 14 years of HIPAA's existence.
Organizations that deal with PHI need to have clearly defined policies and procedures to protect patient data, training to make sure that employees are aware of the rules, and most importantly methods that can be used to monitor that the policies are being followed. If you are the CISO of a healthcare organization you should be asking yourself questions such as:
In the previous settlements of 2011, Massachusetts General agreed to pay a fine of $1,000,o00 and Cignet Health of Prince George's County agreed to a fine of $4,300,000. Clearly HHS is taking these violations much more seriously than had been done in the first 14 years of HIPAA's existence.
Organizations that deal with PHI need to have clearly defined policies and procedures to protect patient data, training to make sure that employees are aware of the rules, and most importantly methods that can be used to monitor that the policies are being followed. If you are the CISO of a healthcare organization you should be asking yourself questions such as:
- Are all of the laptops that access our systems encrypted?
- How do I validate that they are encrypted?
- Are we monitoring access to patient information?
- How do we detect inappropriate access to PHI?
Monday, July 4, 2011
Zero Day by Mark Russinovich
Of course you can tell by reading this blog that I am not a storyteller; and certainly not a novelist. Therefore I preface this review with that caveat that I could not have written Zero Day as well as Mark Russinovich. Zero Day is a thriller surrounding the release of a set of extremely destructive computer viruses. We track the progress of Jeff Aiken, a private security consultant, and Darryl Haugen, a PhD. Computer scientist from MIT working for the Department of Homeland Security, as they try to identify the viruses, determine a solution, and track down the perpetrators. The main flaws of the novel is that the characters are on dimensional and the book is hitting us over the head with a hammer to indicate the potential devastation that society could face as result of a cadre of determined evildoers exploiting the weaknesses of the Internet and computer systems.
As a technical expert, Mark Russinovich is world famous. He is known to us in the security world as one of the cofounders of Sysinternals; which is one of the key solutions available to Windows administrators everywhere. With this technical background, Zero Day describes how a set of evil actors could technically wreck havoc on the computer systems of America and Europe.
The story is engaging and suspenseful and as someone in the security field, I was interested to see where the story led us. Without the importance of the subject matter, the risks to our cyber infrastructure, the book would not be that interesting. The storytelling and actors is too shallow. We have “obligatory” love scenes and one of the “usual suspects,” a Russian cybercriminal, involved. There is limited character development in the story and the bureaucrat that Daryl reports to is as helpful as our stereotypes of bureaucrats would lead us to believe. That being said, I believe like Mark does that the risks we face are severe and the more coverage that they get the better. With that as a backdrop I would recommend this book.
In my opinion, to learn more about the security implications and the deep impact of the Internet on our society, I would first read Daniel Suarez’s two novel set, Daemon and Freedom (TM)
and Freedom (TM) . These provide a much more nuanced look at the good and bad associated with the Internet and our dependence on it.
. These provide a much more nuanced look at the good and bad associated with the Internet and our dependence on it.
As a technical expert, Mark Russinovich is world famous. He is known to us in the security world as one of the cofounders of Sysinternals; which is one of the key solutions available to Windows administrators everywhere. With this technical background, Zero Day describes how a set of evil actors could technically wreck havoc on the computer systems of America and Europe.
The story is engaging and suspenseful and as someone in the security field, I was interested to see where the story led us. Without the importance of the subject matter, the risks to our cyber infrastructure, the book would not be that interesting. The storytelling and actors is too shallow. We have “obligatory” love scenes and one of the “usual suspects,” a Russian cybercriminal, involved. There is limited character development in the story and the bureaucrat that Daryl reports to is as helpful as our stereotypes of bureaucrats would lead us to believe. That being said, I believe like Mark does that the risks we face are severe and the more coverage that they get the better. With that as a backdrop I would recommend this book.
In my opinion, to learn more about the security implications and the deep impact of the Internet on our society, I would first read Daniel Suarez’s two novel set, Daemon
Tuesday, May 31, 2011
Kingpin
Kevin Poulsen's Kingpin is a fascinating look at the world of cybercrime involving credit card theft and fraud. The story is told from two angles. The first is from the perspective of Max Butler, one of the leading cyber criminals of the last ten years, and the second is from the perspective of law enforcement. We follow the path of J. Kevin Mularski, an FBI agent, who leads the effort to track down and ultimately capture Max Butler.
As “Iceman,” Butler ran Carders Market, an online marketplace for illegal credit card data. The book covers many of the high-level techniques that Butler uses to break into systems, invade Point of Sale Systems, and it includes a solid discussion of how SQL injection is used to steal data. In fascinating detail Poulsen covers how Max uses hacking techniques to take over many of the illegal sites that hackers use to buy and sell credit card information, shut down his competitors, and move all of the traffic over to his Carders Market site.
The dual focus on the criminals and the law enforcement efforts to capture them makes the story a page turner, and it reads like a crime novel. Kingpin also covers some of the law enforcement efforts surrounding, Shadowcrew, the online criminal marketplace that was shut down due to the information received from the combination informant / cybercriminal Albert Gonzalez, who would later be arrested and convicted for the TJX and Heartland Payment Systems breaches. The FBI brilliantly set up a VPN for the Shadowcrew service so that they could tap all of the online conversations and identify the evildoers.
Kevin Poulsen certainly knows the hacker underground, as he was convicted in June of 1994 of several computer crimes and was sentenced to over 4 years in prison. Jonathan Littman covered his Kevin’s exploits in The Watchman: The Twisted Life and Crimes of Serial Hacker Kevin Poulsen
As “Iceman,” Butler ran Carders Market, an online marketplace for illegal credit card data. The book covers many of the high-level techniques that Butler uses to break into systems, invade Point of Sale Systems, and it includes a solid discussion of how SQL injection is used to steal data. In fascinating detail Poulsen covers how Max uses hacking techniques to take over many of the illegal sites that hackers use to buy and sell credit card information, shut down his competitors, and move all of the traffic over to his Carders Market site.
The dual focus on the criminals and the law enforcement efforts to capture them makes the story a page turner, and it reads like a crime novel. Kingpin also covers some of the law enforcement efforts surrounding, Shadowcrew, the online criminal marketplace that was shut down due to the information received from the combination informant / cybercriminal Albert Gonzalez, who would later be arrested and convicted for the TJX and Heartland Payment Systems breaches. The FBI brilliantly set up a VPN for the Shadowcrew service so that they could tap all of the online conversations and identify the evildoers.
Kevin Poulsen certainly knows the hacker underground, as he was convicted in June of 1994 of several computer crimes and was sentenced to over 4 years in prison. Jonathan Littman covered his Kevin’s exploits in The Watchman: The Twisted Life and Crimes of Serial Hacker Kevin Poulsen
Sunday, February 20, 2011
The CREATOR OWNER Problem
This post describes the problem caused by the CREATOR OWNER permissions that are set by default in Windows Server 2003 on folders. Take the example here of the Human Resources folder and all of the subdirectories underneath it. This is sensitive data that we want to manage the permissions extremely carefully. The challenge with the CREATOR OWNER permission is that when a user creates a subfolder within a folder that contains this permission, the SID of that User is set to Full permissions on the new folder, even though we had given them only Modify permissions within the "Terminations" folder.

If we look at the security of the "DoneBYSSmith-CO-ON" folder, we can see that Windows Server 2003 has added an Access Control Entry for Sally Smith and given that user Full control.

This is not what we wanted, but Windows does it because the CREATOR OWNER permission was set at the parent folder as shown here.

What we need to do is remove the CREATOR OWNER at the top level folder where inheritance is turned off and then push it down to all of the child objects. The permissions should then look like this at the parent folder. When any user in the grp.Share.HumanResources.Modify group creates a folder, then they will not inherit full permissions, which is normally what we want. They will instead retain just the permissions granted by the group they belong to.

Beware the CREATOR OWNER SID.

If we look at the security of the "DoneBYSSmith-CO-ON" folder, we can see that Windows Server 2003 has added an Access Control Entry for Sally Smith and given that user Full control.

This is not what we wanted, but Windows does it because the CREATOR OWNER permission was set at the parent folder as shown here.

What we need to do is remove the CREATOR OWNER at the top level folder where inheritance is turned off and then push it down to all of the child objects. The permissions should then look like this at the parent folder. When any user in the grp.Share.HumanResources.Modify group creates a folder, then they will not inherit full permissions, which is normally what we want. They will instead retain just the permissions granted by the group they belong to.

Beware the CREATOR OWNER SID.
Subscribe to:
Posts (Atom)